Application field
Cybersecurity, IoT
Technology
Cyberattacks, Machine Learning
Goals
Development of methodologies for assessing the performance of cyberattacks, along with its uncertainty. Profiled attacks relying on machine learning are mainly considered. Methods like cross-validation and Monte Carlo can be exploited to assess the uncertainty and the final aim is to evaluate the vulnerability of an embedded device from the hardware point of view.
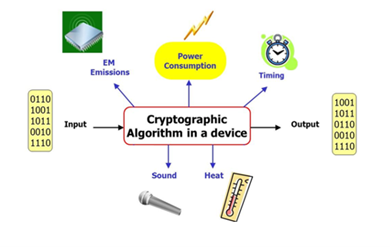
In this process, measurements are strongly involved with reference to the acquisition of power traces or other leakages during the operation of the device under test. Then, data processing has a crucial role in the vulnerability assessment in case of presence or absence of countermeasures.
Furthermore, analysis of a sensor network behavior in the event of cyberattacks, such as Denial of Service or Man-In-The-Middle is critical for development of first reaction behavior methodologies.
Development of methodologies for anomaly detection, intrusion control, and security enhancement of IoT devices and sensor networks using machine learning.
Activities
- Measurement and collection of on field data during sensitive operations (e.g Power Traces).
- Pre-processing of data and identification of points of interest (e.g. by means of signal-to-noise ratio analysis)
- Classification of pre-processed data
- Guessing entropy and uncertainty assessment for bytes of AES key
- Implementation of a secure smart sensor network for green IoT
- Implementation of machine learning models for anomaly detection and intrusion control
Challenges
- Improving the security of IoT devices
Bibliography
- Arpaia, P., Caputo F., Cioffi A., Esposito A. & Isgrò F. (submitted). Uncertainty analysis in cryptographic key recovery for machine learning-based power measurements attacks. IEEE Transactions for Instrumentation and Measurement
- Arpaia P., Bonavolontà F., Cioffi A., & Moccaldi N (2021). Power Measurement-Based Vulnerability Assessment of IoT Medical Devices at Varying Countermeasures for Cybersecurity, IEEE Transactions for Instrumentation and Measurement, p. 9452159
- Arpaia P., Bonavolontà F., Cioffi A., & Moccaldi N (2021). Reproducibility Enhancement by Optimized Power Analysis Attacks in Vulnerability Assessment of IoT Transducers, IEEE Transactions for Instrumentation and Measurement, p. 9521880
- Arpaia P., Bonavolontà F., & Cioffi A., (2020). Problems of the Advanced Encryption Standard in protecting Internet of Things sensor networks, Measurement, p. 107853.
Foto
Figura 1: Side Channel Leaks
Figura 2: Uncertainty assessment
Figura 3: Automatic Measure Station





